© 2011 Microchip Technology Inc.
DS41097D-page 1
HCS320
FEATURES
Security
• Programmable 28-bit serial number
• Programmable 64-bit encryption key
• Each transmission is unique
• 66-bit transmission code length
• 32-bit hopping code
• 34-bit fixed code (28-bit serial number,
4-bit function code, 2-bit status)
• Encryption keys are read protected
Operating
• 3.5V - 13.0V operation
• Shift key and three inputs
• 16 functions available
• Selectable baud rate
• Automatic code word completion
• Battery low signal transmitted to receiver
• Battery low indication on LED
• Non-volatile synchronization data
Other
• Easy-to-use programming interface
• On-chip EEPROM
• On-chip oscillator and timing components
• Button inputs have internal pull-down resistors
• Current limiting on LED output
• Low external component cost
Typical Applications
The HCS320 is ideal for Remote Keyless Entry (RKE)
applications. These applications include:
• Automotive RKE systems
• Automotive alarm systems
• Automotive immobilizers
• Gate and garage door openers
• Identity tokens
• Burglar alarm systems
DESCRIPTION
The HCS320 from Microchip Technology Inc. is a code
hopping encoder designed for secure Remote Keyless
Entry (RKE) systems. The HCS320 utilizes the code
hopping technology which incorporates high security, a
small package outline, and low cost, to make this
device a perfect solution for unidirectional remote key-
less entry systems and access control systems.
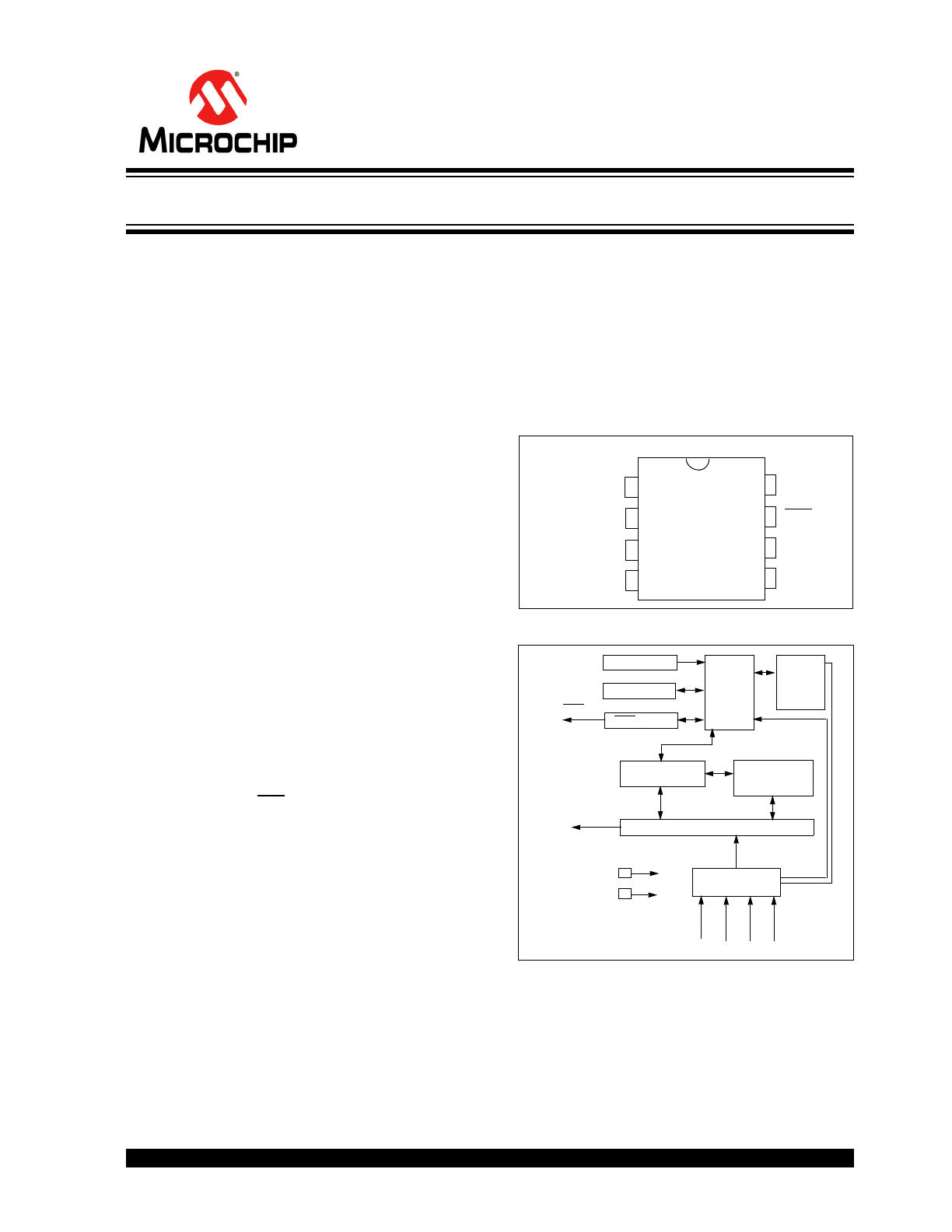
PACKAGE TYPES
HCS320 BLOCK DIAGRAM
The HCS320 combines a 32-bit hopping code gener-
ated by a nonlinear encryption algorithm, with a 28-bit
serial number and six status bits to create a 66-bit
transmission stream. The length of the transmission
eliminates the threat of code scanning and the code
hopping mechanism makes each transmission unique,
thus rendering code capture and resend (code grab-
bing) schemes useless.
1
2
3
4
8
7
6
5
S0
S1
S2
SHIFT
V
DD
LED
PWM
V
SS
PDIP, SOIC
HCS3
20
V
SS
V
DD
Oscillator
RESET circuit
LED driver
Controller
Power
latching
and
switching
Button input port
32-bit shift register
Encoder
EEPROM
PWM
LED
SHIFT S
2
S
1
S
0
K
EE
L
OQ®
Code Hopping Encoder

HCS320
DS41097D-page 2
© 2011 Microchip Technology Inc.
The crypt key, serial number and configuration data are
stored in an EEPROM array which is not accessible via
any external connection. The EEPROM data is pro-
grammable but read-protected. The data can be veri-
fied only after an automatic erase and programming
operation. This protects against attempts to gain
access to keys or manipulate synchronization values.
The HCS320 provides an easy-to-use serial interface
for programming the necessary keys, system parame-
ters and configuration data.
1.0
SYSTEM OVERVIEW
Key Terms
The following is a list of key terms used throughout this
data sheet. For additional information on K
EE
L
OQ®
and
Code Hopping, refer to Technical Brief 3 (TB003).
• RKE - Remote Keyless Entry
• Button Status - Indicates what button input(s)
activated the transmission. Encompasses the 4
button status bits S3, S2, S1 and S0 (Figure 4-2).
• Code Hopping - A method by which a code,
viewed externally to the system, appears to
change unpredictably each time it is transmitted.
• Code word - A block of data that is repeatedly
transmitted upon button activation (Figure 4-1).
• Transmission - A data stream consisting of
repeating code words (Figure 9-2).
• Crypt key - A unique and secret 64-bit number
used to encrypt and decrypt data. In a symmetri-
cal block cipher such as the K
EE
L
OQ
algorithm,
the encryption and decryption keys are equal and
will therefore be referred to generally as the crypt
key.
• Encoder - A device that generates and encodes
data.
• Encryption Algorithm - A recipe whereby data is
scrambled using a crypt key. The data can only be
interpreted by the respective decryption algorithm
using the same crypt key.
• Decoder - A device that decodes data received
from an encoder.
• Decryption algorithm - A recipe whereby data
scrambled by an encryption algorithm can be
unscrambled using the same crypt key.
• Learn – Learning involves the receiver calculating
the transmitter’s appropriate crypt key, decrypting
the received hopping code and storing the serial
number, synchronization counter value and crypt
key in EEPROM. The K
EE
L
OQ
product family facil-
itates several learning strategies to be imple-
mented on the decoder. The following are
examples of what can be done.
- Simple Learning
The receiver uses a fixed crypt key, common
to all components of all systems by the same
manufacturer, to decrypt the received code
word’s encrypted portion.
- Normal Learning
The receiver uses information transmitted
during normal operation to derive the crypt
key and decrypt the received code word’s
encrypted portion.
- Secure Learn
The transmitter is activated through a special
button combination to transmit a stored 60-bit
seed value used to generate the transmitter’s
crypt key. The receiver uses this seed value
to derive the same crypt key and decrypt the
received code word’s encrypted portion.
• Manufacturer’s code – A unique and secret 64-
bit number used to generate unique encoder crypt
keys. Each encoder is programmed with a crypt
key that is a function of the manufacturer’s code.
Each decoder is programmed with the manufac-
turer code itself.
The HCS320 code hopping encoder is designed specif-
ically for keyless entry systems; primarily vehicles and
home garage door openers. The encoder portion of a
keyless entry system is integrated into a transmitter,
carried by the user and operated to gain access to a
vehicle or restricted area. The HCS320 is meant to be
a cost-effective yet secure solution to such systems,
requiring very few external components (Figure 2-1).
Most low-end keyless entry transmitters are given a
fixed identification code that is transmitted every time a
button is pushed. The number of unique identification
codes in a low-end system is usually a relatively small
number. These shortcomings provide an opportunity
for a sophisticated thief to create a device that ‘grabs’
a transmission and retransmits it later, or a device that
quickly ‘scans’ all possible identification codes until the
correct one is found.
The HCS320 on the other hand, employs the K
EE
L
OQ
code hopping technology coupled with a transmission
length of 66 bits to virtually eliminate the use of code
‘grabbing’ or code ‘scanning’. The high security level of
the HCS320 is based on the patented K
EE
L
OQ
technol-
ogy. A block cipher based on a block length of 32 bits
and a key length of 64 bits is used. The algorithm
obscures the information in such a way that even if the
transmission information (before coding) differs by only
one bit from that of the previous transmission, the next
© 2011 Microchip Technology Inc.
DS41097D-page 3
HCS320
coded transmission will be completely different. Statis-
tically, if only one bit in the 32-bit string of information
changes, greater than 50 percent of the coded trans-
mission bits will change.
As indicated in the block diagram on page one, the
HCS320 has a small EEPROM array which must be
loaded with several parameters before use; most often
programmed by the manufacturer at the time of produc-
tion. The most important of these are:
• A 28-bit serial number, typically unique for every
encoder
• A crypt key
• An initial 16-bit synchronization value
• A 16-bit configuration value
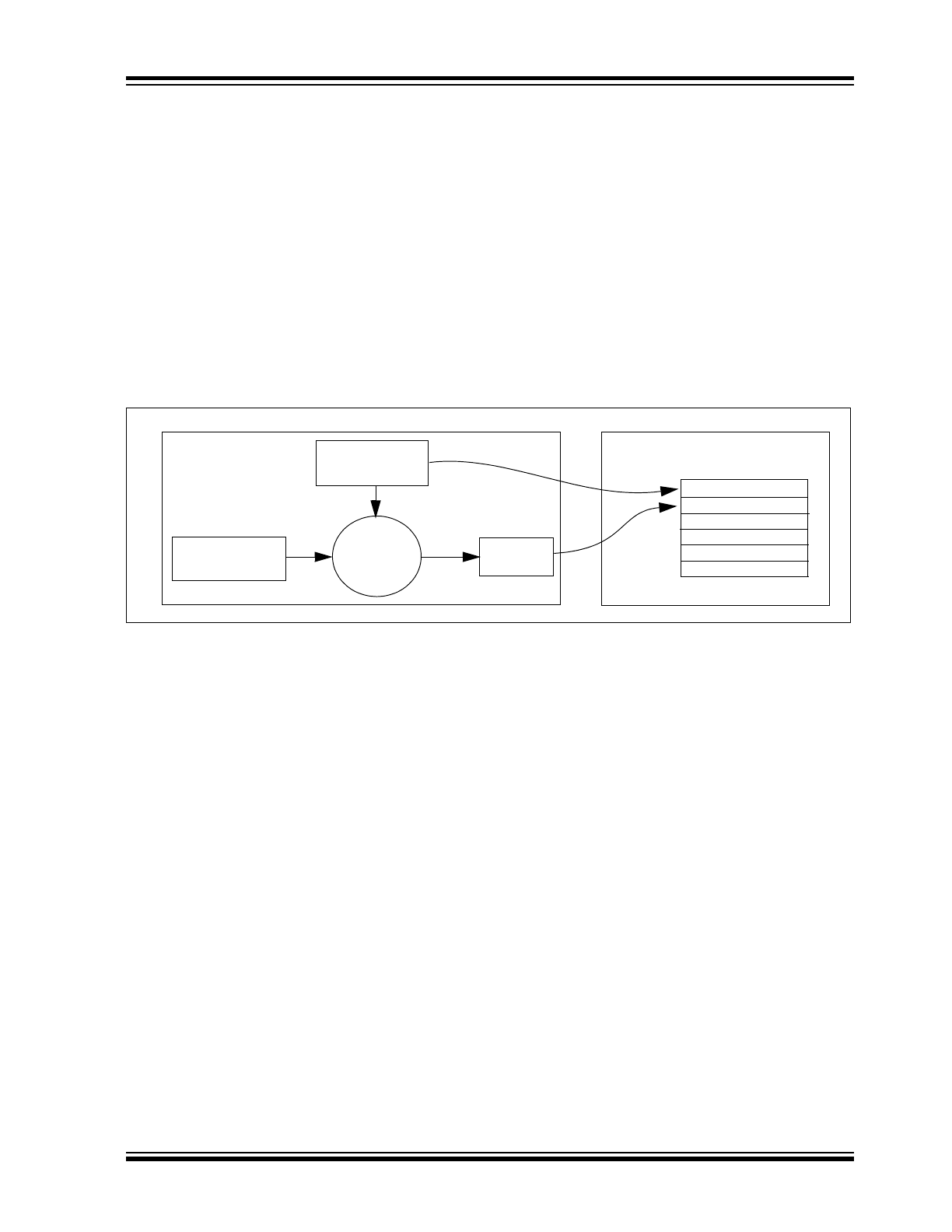
The crypt key generation typically inputs the transmitter
serial number and 64-bit manufacturer’s code into the
key generation algorithm (Figure 1-1). The manufac-
turer’s code is chosen by the system manufacturer and
must be carefully controlled as it is a pivotal part of the
overall system security.
FIGURE 1-1:
CREATION AND STORAGE OF CRYPT KEY DURING PRODUCTION
The 16-bit synchronization counter is the basis behind
the transmitted code word changing for each transmis-
sion; it increments each time a button is pressed. Due
to the code hopping algorithm’s complexity, each incre-
ment of the synchronization value results in greater
than 50% of the bits changing in the transmitted code
word.
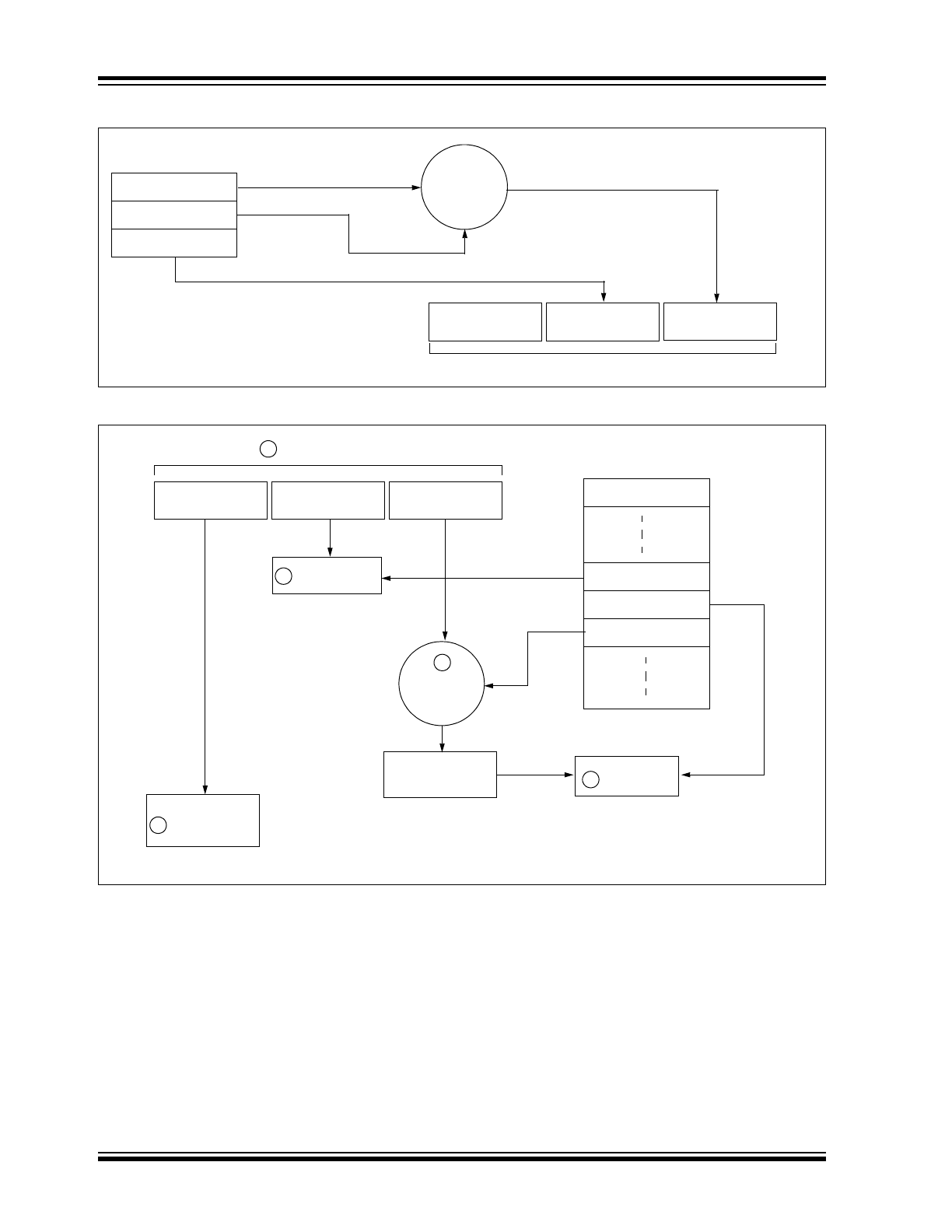
Figure 1-2 shows how the key values in EEPROM are
used in the encoder. Once the encoder detects a button
press, it reads the button inputs and updates the syn-
chronization counter. The synchronization counter and
crypt key are input to the encryption algorithm and the
output is 32 bits of encrypted information. This data will
change with every button press, its value appearing
externally to ‘randomly hop around’, hence it is referred
to as the hopping portion of the code word. The 32-bit
hopping code is combined with the button information
and serial number to form the code word transmitted to
the receiver. The code word format is explained in
greater detail in Section 4.0.
A receiver may use any type of controller as a decoder,
but it is typically a microcontroller with compatible firm-
ware that allows the decoder to operate in conjunction
with an HCS320 based transmitter. Section 7.0
provides detail on integrating the HCS320 into a sys-
tem.
A transmitter must first be ‘learned’ by the receiver
before its use is allowed in the system. Learning
includes calculating the transmitter’s appropriate crypt
key, decrypting the received hopping code and storing
the serial number, synchronization counter value and
crypt key in EEPROM.
In normal operation, each received message of valid
format is evaluated. The serial number is used to deter-
mine if it is from a learned transmitter. If from a learned
transmitter, the message is decrypted and the synchro-
nization counter is verified. Finally, the button status is
checked to see what operation is requested. Figure 1-
3 shows the relationship between some of the values
stored by the receiver and the values received from the
transmitter.
Transmitter
Manufacturer’s
Serial Number
Code
Crypt
Key
Key
Generation
Algorithm
Serial Number
Crypt Key
Sync Counter
.
.
.
HCS320
Production
Programmer
EEPROM Array
HCS320
DS41097D-page 4
© 2011 Microchip Technology Inc.
FIGURE 1-2:
BUILDING THE TRANSMITTED CODE WORD (ENCODER)
FIGURE 1-3:
BASIC OPERATION OF RECEIVER (DECODER)
NOTE: Circled numbers indicate the order of execution.
Button Press
Information
EEPROM Array
32 Bits
Encrypted Data
Serial Number
Transmitted Information
Crypt Key
Sync Counter
Serial Number
K
EE
L
OQ®
Encryption
Algorithm
Button Press
Information
EEPROM Array
Manufacturer Code
32 Bits of
Encrypted Data
Serial Number
Received Information
Decrypted
Synchronization
Counter
Check for
Match
Sync Counter
Serial Number
K
EE
L
OQ®
Decryption
Algorithm
1
3
4
Check for
Match
2
Perform Function
Indicated by
button press
5
Crypt Key
© 2011 Microchip Technology Inc.
DS41097D-page 5
HCS320
2.0
DEVICE OPERATION
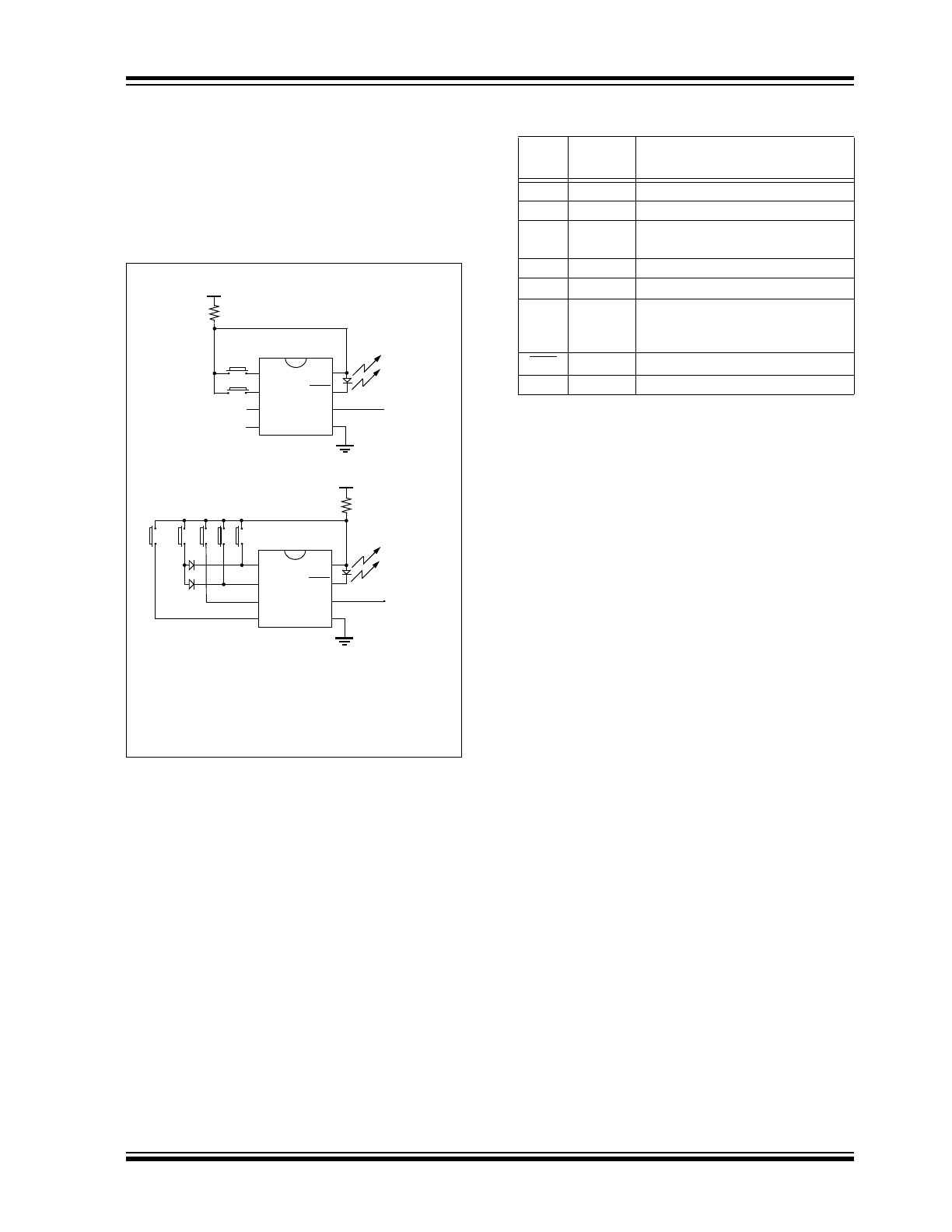
As shown in the typical application circuits (Figure 2-1),
the HCS320 is a simple device to use. It requires only
the addition of buttons and RF circuitry for use as the
transmitter in your security application. A description of
each pin is described in Table 2-1.
FIGURE 2-1:
TYPICAL CIRCUITS
TABLE 2-1:
PIN DESCRIPTIONS
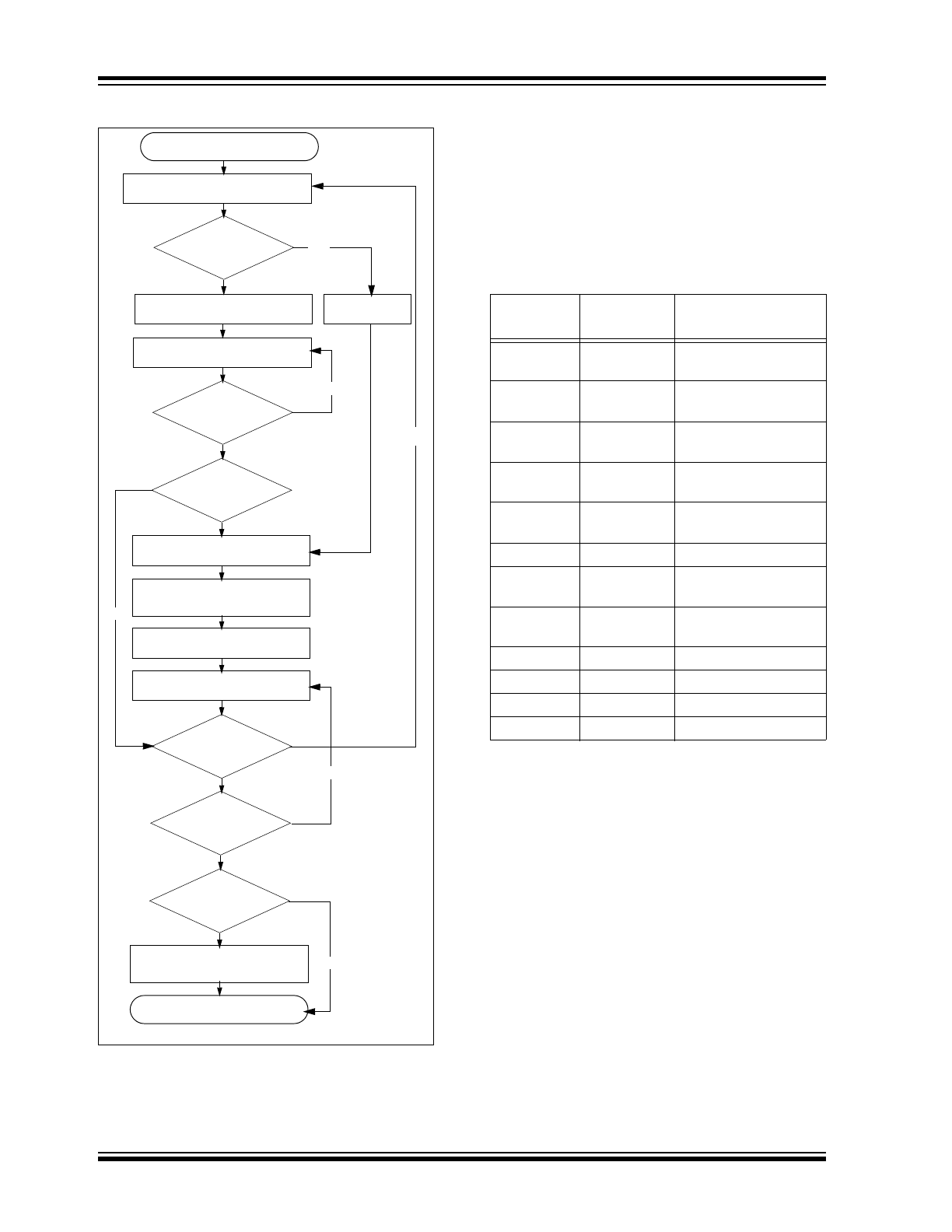
The HCS320 will wake-up upon detecting a button
press and delay approximately 10 ms for button
debounce (Figure 2-2). The synchronization counter,
discrimination value and button information will be
encrypted to form the hopping code. The hopping code
portion will change every transmission, even if the
same button is pushed again. A code word that has
been transmitted will not repeat for more than 64K
transmissions. This provides more than 18 years of use
before a code is repeated; based on 10 operations per
day. Overflow information sent from the encoder can be
used to extend the number of unique transmissions to
more than 192K.
If in the transmit process it is detected that a new but-
ton(s) has been pressed, a RESET will immediately
occur and the current code word will not be completed.
Please note that buttons removed will not have any
effect on the code word unless no buttons remain
pressed; in which case the code word will be completed
and the power-down will occur.
B0
Tx out
S0
S1
S2
SHIFT
LED
V
DD
PWM
V
SS
2 button remote control
B1
Tx out
S0
S1
S2
SHIFT
LED
V
DD
PWM
V
SS
5 button remote control
(1)
B3 B2 B1 B0
Note 1: The full 16 function codes are
implemented using the shift button.
2: Resistor R is recommended for current
limiting.
+12V
+12V
R
(2)
R
(2)
SHIFT
Name
Pin
Number
Description
S0
1
Switch input 0
S1
2
Switch input 1
S2
3
Switch input 2/Clock pin when in
Programming mode
SHIFT
4
Switch input for Shift
V
SS
5
Ground reference
PWM
6
Pulse Width Modulation (PWM)
output pin / Data pin for
Programming mode
LED
7
Cathode connection for LED
V
DD
8
Positive supply voltage
HCS320
DS41097D-page 6
© 2011 Microchip Technology Inc.
FIGURE 2-2:
ENCODER OPERATION
3.0
EEPROM MEMORY
ORGANIZATION
The HCS320 contains 192 bits (12 x 16-bit words) of
EEPROM memory (Table 3-1). This EEPROM array is
used to store the encryption key information,
synchronization value, etc. Further descriptions of the
memory array is given in the following sections.
TABLE 3-1:
EEPROM MEMORY MAP
3.1
KEY_0 - KEY_3 (64-Bit Crypt Key)
The 64-bit crypt key is used to create the encrypted
message transmitted to the receiver. This key is calcu-
lated and programmed during production using a key
generation algorithm. The key generation algorithm
may be different from the K
EE
L
OQ
algorithm. Inputs to
the key generation algorithm are typically the transmit-
ter’s serial number and the 64-bit manufacturer’s code.
While the key generation algorithm supplied from
Microchip is the typical method used, a user may elect
to create their own method of key generation. This may
be done providing that the decoder is programmed with
the same means of creating the key for
decryption purposes.
Power-Up
RESET and Debounce Delay
(10 ms)
Encrypt With
Load Transmit Register
Buttons
Added?
All
Buttons
Released?
(Button pressed) Set TX:= OFF
Transmit
Stop
Crypt Key
Complete Code
Word Transmission
No
Transmit
Button Pressed?
Increment Shift Level
Stop Transmit
Shift
Button Pressed?
TX=ON?
Update Sync Info
TX=ON?
Set TX:=ON
No
No
No
Yes
Yes
No
Yes
Yes
No
Yes
Yes
WORD
ADDRESS
MNEMONIC
DESCRIPTION
0
KEY_0 64-bit
encryption
key
(word 0) LSb’s
1
KEY_1
64-bit encryption key
(word 1)
2
KEY_2
64-bit encryption key
(word 2)
3
KEY_3 64-bit
encryption
key
(word 3) MSb’s
4
SYNC
16-bit synchronization
value
5
RESERVED Set to 0000H
6
SER_0
Device Serial Number
(word 0) LSb’s
7
SER_1(Note) Device Serial Number
(word 1) MSb’s
8
—
Not used
9
—
Not used
10
RESERVED Set to 0000H
11
CONFIG
Configuration Word
Note:
The MSB of the serial number contains a
bit used to select the Auto-shutoff timer.

© 2011 Microchip Technology Inc.
DS41097D-page 7
HCS320
3.2
SYNC (Synchronization Counter)
This is the 16-bit synchronization value that is used to
create the hopping code for transmission. This value
will be changed after every transmission.
3.3
Reserved
Must be initialized to 0000H.
3.4
SER_0, SER_1
(Encoder Serial Number)
SER_0 and SER_1 are the lower and upper words of
the device serial number, respectively. Although there
are 32 bits allocated for the serial number, only the
lower order 28 bits are transmitted. The serial number
is meant to be unique for every transmitter. The Most
Significant bit of the serial number (Bit 31) is used to
turn the Auto-shutoff timer on or off.
3.4.1
AUTO-SHUTOFF TIMER ENABLE
The Most Significant bit of the serial number (Bit 31) is
used to turn the Auto-shutoff timer on or off. This timer
prevents the transmitter from draining the battery
should a button get stuck in the on position for a long
period of time. The time period is approximately
25 seconds, after which the device will go to the Time-
out mode. When in the Time-out mode, the device will
stop transmitting, although since some circuits within
the device are still active, the current draw within the
Shutoff mode will be more than Standby mode. If the
Most Significant bit in the serial number is a one, then
the Auto-shutoff timer is enabled, and a zero in the
Most Significant bit will disable the timer. The length of
the timer is not selectable.
3.5
CONFIG (Configuration Word)
The Configuration Word is a 16-bit word stored in
EEPROM array that is used by the device to store infor-
mation used during the encryption process, as well as
the status of option configurations. The following sec-
tions further explain these bits.
TABLE 3-2:
CONFIGURATION WORD
3.5.1
DISCRIMINATION VALUE
(DISC0 TO DISC9)
The discrimination value aids the post-decryption
check on the decoder end. It may be any value, but in
a typical system it will be programmed as the 10 Least
Significant bits of the serial number. Values other than
this must be separately stored by the receiver when a
transmitter is learned. The discrimination bits are part
of the information that form the encrypted portion of the
transmission (Figure 4-2). After the receiver has
decrypted a transmission, the discrimination bits are
checked against the receiver’s stored value to verify
that the decryption process was valid. If the discrimina-
tion value was programmed as the 10 LSb’s of the
serial number then it may merely be compared to the
respective bits of the received serial number; saving
EEPROM space.
3.5.2
OVERFLOW BITS (OVR0, OVR1)
The overflow bits are used to extend the number of
possible synchronization values. The synchronization
counter is 16 bits in length, yielding 65,536 values
before the cycle repeats. Under typical use of
10 operations a day, this will provide nearly 18 years of
use before a repeated value will be used. Should the
system designer conclude that is not adequate, then
the overflow bits can be utilized to extend the number
Bit Number
Bit Description
0
Discrimination Bit 0
1
Discrimination Bit 1
2
Discrimination Bit 2
3
Discrimination Bit 3
4
Discrimination Bit 4
5
Discrimination Bit 5
6
Discrimination Bit 6
7
Discrimination Bit 7
8
Discrimination Bit 8
9
Discrimination Bit 9
10
Overflow Bit 0 (OVR0)
11
Overflow Bit 1 (OVR1)
12
Low Voltage Trip Point Select
(V
LOW
SEL
)
13
Baud rate Select Bit 0 (BSL0)
14
Baud rate Select Bit 1 (BSL1)
15
Reserved, set to 0
HCS320
DS41097D-page 8
© 2011 Microchip Technology Inc.
of unique values. This can be done by programming
OVR0 and OVR1 to 1s at the time of production. The
encoder will automatically clear OVR0 the first time that
the synchronization value wraps from 0xFFFF to
0x0000 and clear OVR1 the second time the counter
wraps. Once cleared, OVR0 and OVR1 cannot be set
again, thereby creating a permanent record of the
counter overflow. This prevents fast cycling of 64K
counter. If the decoder system is programmed to track
the overflow bits, then the effective number of unique
synchronization values can be extended to 196,608.
3.5.3
BAUD RATE SELECT BITS (BSL0,
BSL1)
BSL0 and BSL1 select the speed of transmission and
the code word blanking. Table 3-3 shows how the bits
are used to select the different baud rates and
Section 5.6 provides detailed explanation in code word
blanking.
TABLE 3-3:
BAUD RATE SELECT
3.5.4
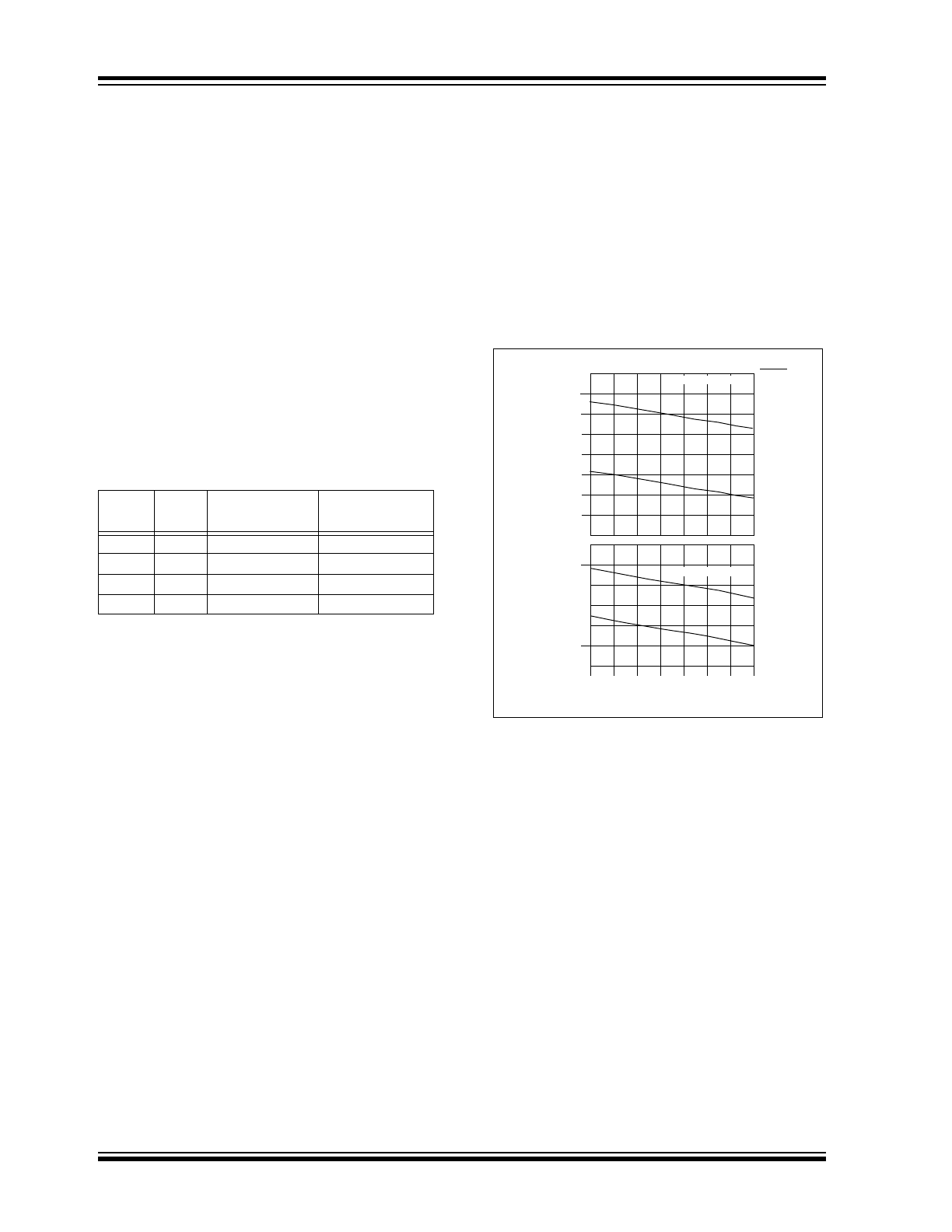
LOW VOLTAGE TRIP POINT
SELECT
The low voltage trip point select bit is used to tell the
HCS320 what V
DD
level is being used. This information
will be used by the device to determine when to send
the voltage low signal to the receiver. When this bit is
set to a one, the V
DD
level is assumed to be operating
from a 9.0 volt or 12.0 volt V
DD
level. If the bit is set low,
then the V
DD
level is assumed to be 6.0 volts. Refer to
Figure 3-1 for voltage trip point.
FIGURE 3-1:
VOLTAGE TRIP POINTS
BY CHARACTERIZATION)
BSL1
BSL0
Basic Pulse
Element
Code Words
Transmitted
0
0
400
μs
All
0
1
200
μs
1 out of 2
1
0
100
μs
1 out of 2
1
1
100
μs
1 out of 4
-40
20
40
100
8.5
7.5
8.0
7.0
9.0
2.5
3.0
3.5
4.0
V
LOW
Temp (C)
Volts (V)
V
LOW
sel = 1
V
LOW
sel = 0
4.5
-20
0
60
80
5.0
5.5
Max
Min
Max
Min
© 2011 Microchip Technology Inc.
DS41097D-page 9
HCS320
4.0
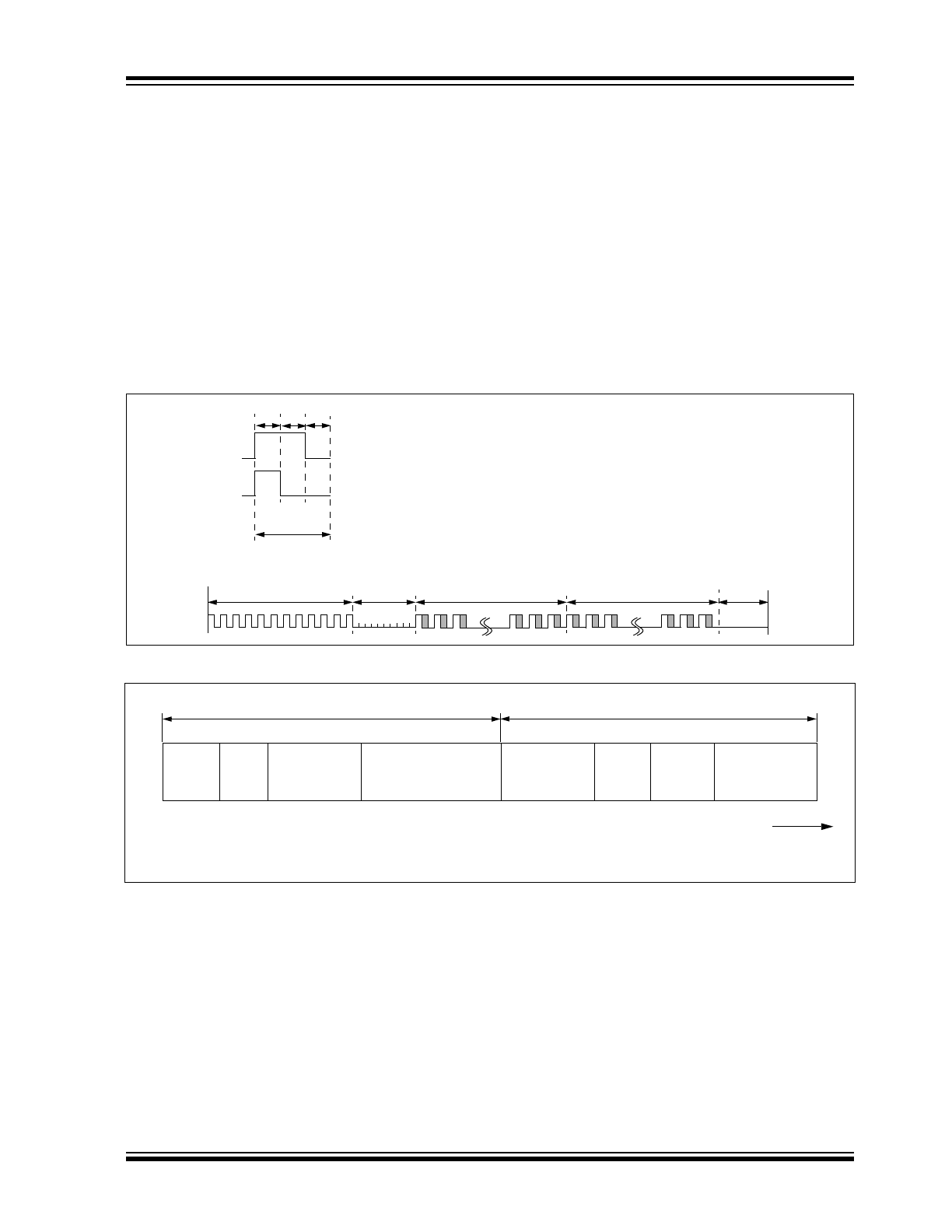
TRANSMITTED WORD
4.1
Code Word Format
The HCS320 code word is made up of several parts
(Figure 4-1). Each code word contains a 50% duty
cycle preamble, a header, 32 bits of encrypted data and
34 bits of fixed data followed by a guard period before
another code word can begin. Refer to Table 9-3 for
code word timing.
4.2
Code Word Organization
The HCS320 transmits a 66-bit code word when a
button is pressed. The 66-bit word is constructed from
a Fixed Code portion and an Encrypted Code portion
(Figure 4-2).
The 32 bits of Encrypted Data are generated from 4
button bits, 12 discrimination bits and the 16-bit sync
value. The encrypted portion alone provides up to four
billion changing code combinations.
The 34 bits of Fixed Code Data are made up of 2 sta-
tus bits, 4 button bits and the 28-bit serial number. The
fixed and encrypted sections combined increase the
number of code combinations to 7.38 x 10
19
.
FIGURE 4-1:
CODE WORD FORMAT
FIGURE 4-2:
CODE WORD ORGANIZATION
LOGIC ‘0’
LOGIC ‘1’
Bit
Period
Preamble
Header
Encrypted Portion
of Transmission
Fixed Portion of
Transmission
Guard
Time
T
P
T
H
T
HOP
T
FIX
T
G
T
E
T
E
T
E
50% Duty Cycle
Repeat
(1-bit)
V
LOW
(1-bit)
Function
Code
(4-bit)
Serial Number
(28 bits)
Function
Code
(4-bit)
OVR
(2 bits)
DISC
(10 bits)
Sync Counter
(16 bits)
34 bits of Fixed Portion
32 bits of Encrypted Portion
66 Data bits
Transmitted
LSb first.
LSb
MSb
HCS320
DS41097D-page 10
© 2011 Microchip Technology Inc.
4.3
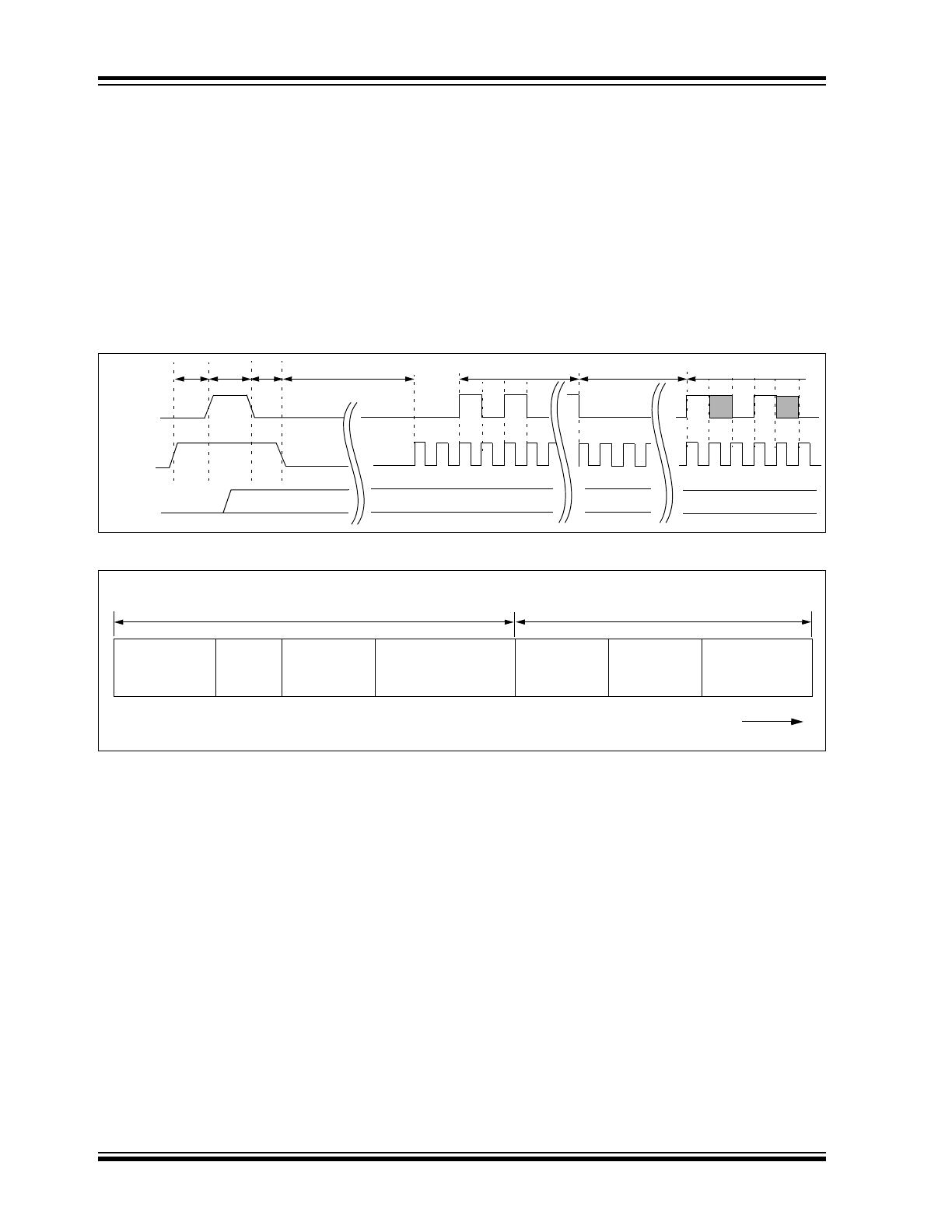
Synchronous Transmission Mode
Synchronous Transmission mode can be used to clock
the code word out using an external clock.
To enter Synchronous Transmission mode, the Pro-
gramming mode start-up sequence must be executed
as shown in Figure 4-3. If either S1 or S0 is set on the
falling edge of S2, the device enters Synchronous
Transmission mode. In this mode, it functions as a nor-
mal transmitter, with the exception that the timing of the
PWM data string is controlled externally and 16 extra
bits are transmitted at the end with the code word.
The button code will be the S0, S1 value at the falling
edge of S2. The timing of the PWM data string is con-
trolled by supplying a clock on S2 and should not
exceed 20 kHz. The code word is the same as in PWM
mode with 16 reserved bits at the end of the word. The
reserved bits can be ignored. When in Synchronous
Transmission mode S2 should not be toggled until all
internal processing has been completed as shown in
Figure 4-4.
FIGURE 4-3:
SYNCHRONOUS TRANSMISSION MODE
FIGURE 4-4:
CODE WORD ORGANIZATION (SYNCHRONOUS TRANSMISSION MODE)
“01,10,11”
PWM
S2
S[1:0]
T
PS
T
PH
1 T
PH
2
t = 50ms
Preamble
Header
Data
Reserved
(16 bits)
Padding
(2 bits)
Function
Code
(4-bit)
Serial Number
(28 bits)
Function
Code
(4-bit)
DISC+ OVR
(12 bits)
Sync Counter
(16 bits)
82 Data bits
Transmitted
LSb first.
LSb
MSb
Fixed Portion
Encrypted Portion
